A few weeks ago, I got a text message on my mobile. It said it was from my credit card company (and it had the right one). It said they had to talk with me urgently about my account, and I should call a given phone number as soon as possible.
In other words, it sure looked like someone was phishing for something... except that they did have the credit card brand correct. Chance, perhaps?
I did what you should do if you get one of those: I ignored the phone number in the message, pulled out my credit card, and called the customer service number on that. I told them what I got. They confirmed that it was from them — it was legitimate. They had flagged my account for unusual activity because of two charges from that morning, and they wanted me to confirm that I had my card with me, and that I had, indeed, made those charges. I did so, and all was well.
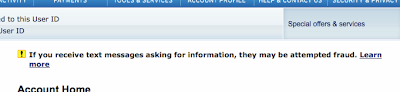
I’ve since logged into my account on their web site, and what do I see?
Clicking on the “Learn more” link gets me to a page that warns me about phishing scams. Among other things, it says this:
Text message verbiage varies, but may direct users to a web site or phone number, and usually contains something that claims to require immediate attention.Ignoring the incorrect use of “verbiage”, this warning is telling me that these fraudulent messages do... exactly what their legitimate message did.
I call this “two-faced security” — security that on the one side warns me to beware of fraud, and on the other side encourages me to do exactly what the fraudsters would like. And I see it all the time.
The legitimate message should, in fact, have told me to do what I actually did. It should not have given me a phone number at all, but should have told me to call the number on my card. It should have given me instructions for finding the correct number out of band ("Go to our web site..."), in the event that my card was missing. We all know that the first thing I’ll have to do when I call the customer service department is give them my account number, possibly along with other personal information such as my name and address. If the “customer service department” I’ve called is actually the phisher’s, taken from their text message, that’s not good for me.
Of course, they go on to tell me what they’re doing to protect me:
[We are] serious about account safety. That’s why we’re requiring all Account Online users to create security questions. We may periodically ask you to answer those questions in Account Online as a quick identity check. That way, when you drop in to do business, we’ll know it’s you.If you’ve been paying attention here, you’ll know how well those questions work... or don’t. But even apart from that, there’s a problem: as I said above, giving the account number is the first thing we’re used to doing when we call. Name and address next. By the time we get to the “security questions”, and realize that the bad guys haven’t asked them, it’s too late. Security doesn’t come from noticing the absence of something, because we’ll never notice until the horse is out of the barn.
The way to thwart this sort of attack is
- for us to learn not to trust anything that’s sent to us, and use only contact information we’ve received separately, which we already trust, and
- for our banks, credit card companies, and other institutions to stop training us to violate number 1.


Comments